SonarQube Plugin
DeepScan provides a SonarQube plugin enabling in-depth analysis for JavaScript and TypeScript in your SonarQube platform.
System Requirements
Operating System
- Windows
- Linux
SonarQube
- Version 8.9 or above
Java
- Oracle JRE 11 or above
- OpenJDK 11 or above
- Windows
- Linux
- Version 8.9 or above
Java
- Oracle JRE 11 or above
- OpenJDK 11 or above
- Oracle JRE 11 or above
- OpenJDK 11 or above
Installation
Let's say you installed SonarQube in /opt/sonarqube.
Installing the plugin
Copy the SonarQube DeepScan plugin into the SonarQube plugins directory and restart the SonarQube server.
cp sonar-deepscan-plugin-x.x.x.jar /opt/sonarqube/extensions/plugins
When the SonarQube server is up and you log in with an administrator account, you will see the plugin information in Administration > Marketplace.
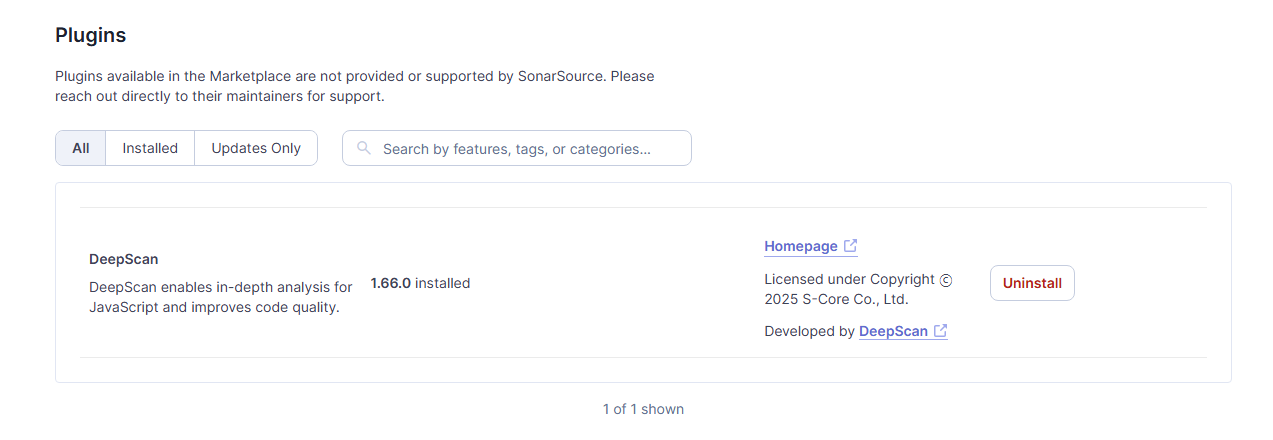
Registering the license
A license key is required to run the SonarQube DeepScan plugin. If a valid license key is not registered, license errors will occur when executing the SonarQube analysis.
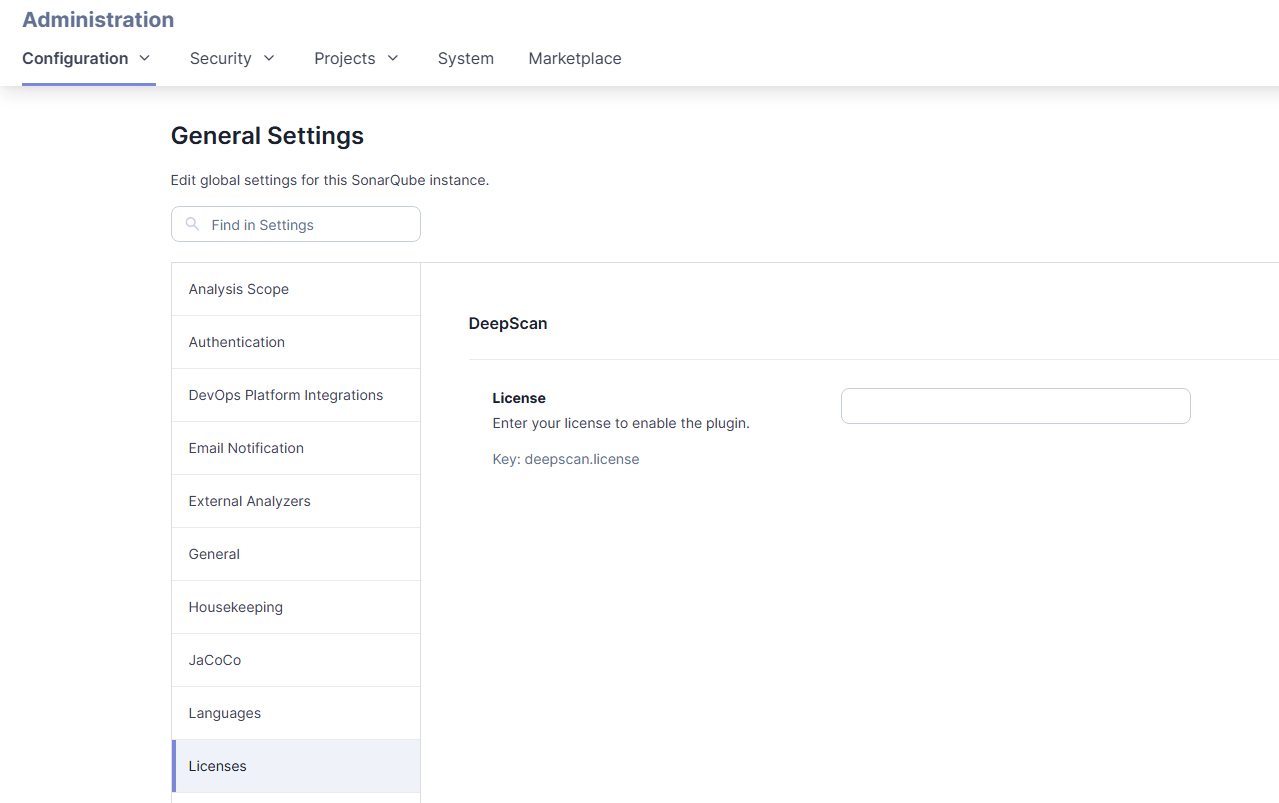
In DeepScan tab of Administration > Configuration > General Settings > Licenses, enter and save the license key in the License field.
Setting the default Quality Profile
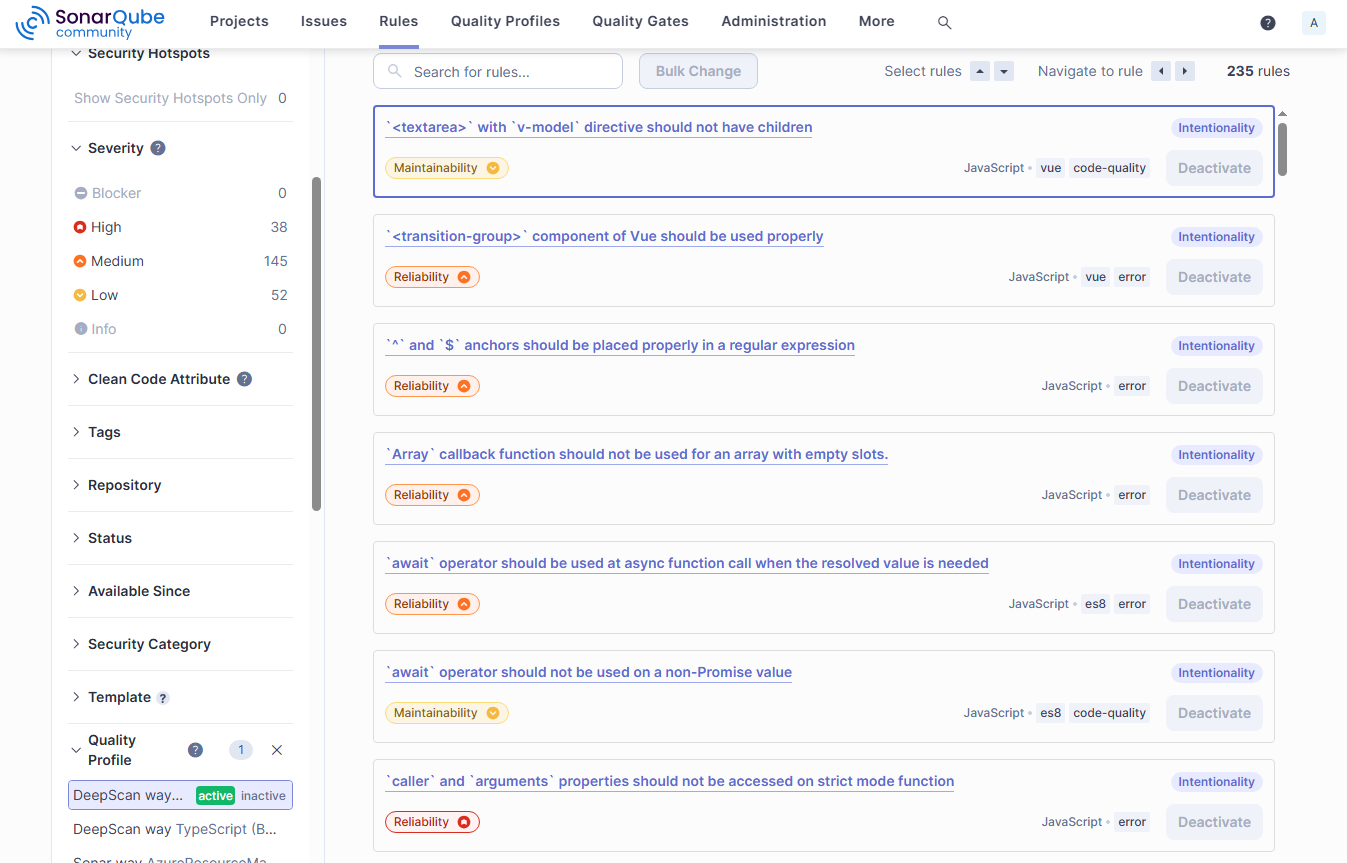
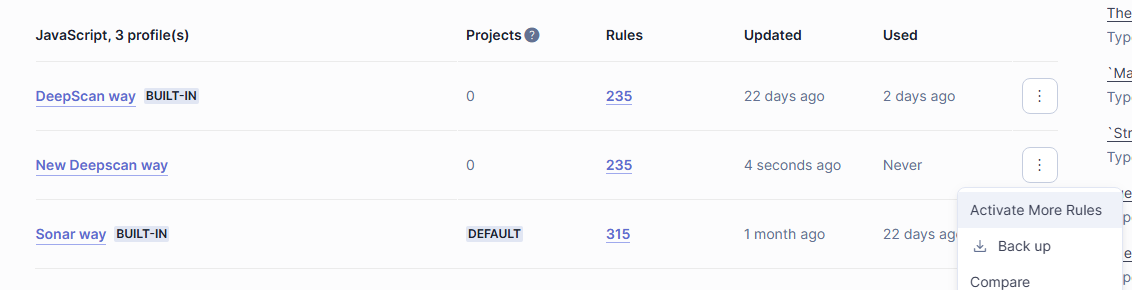
Once installed, you can go to Quality Profiles and see the DeepScan way quality profile under JavaScript and TypeScript.
However, it is not the default profile so DeepScan does not apply when analyzing JavaScript/TypeScript projects. You can set the project's quality profile separately, but if you set the DeepScan way as the default one, then it will apply to all the projects.
To set the default quality profile, log in with administrator permissions and click Set as Default menu on the right of the profile. This should be applied for each of JavaScript and TypeScript languages.
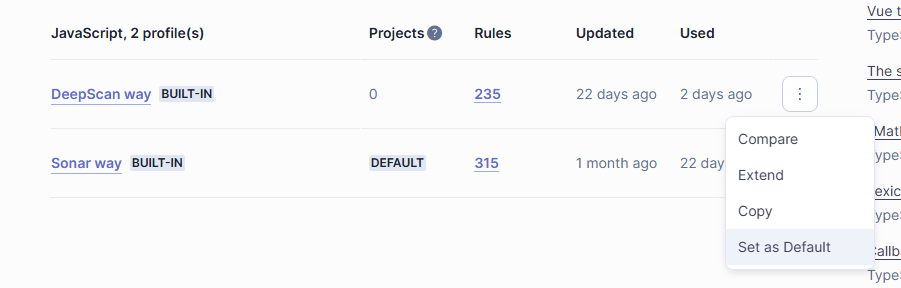
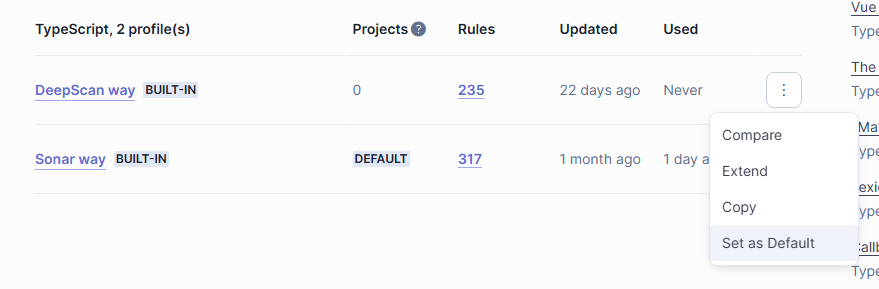
When you click the Rules column value of DeepScan way, you can view the list of DeepScan rules.
Upgrading
Delete the existing plugin and follow the above installation process with the new plugin file.
SonarQube apply the newly added DeepScan rules in the upgraded plugin.
However, if you have used a new profile which modifies the previous profile (such as a severity), click Activate More Rules button to activate more rules.
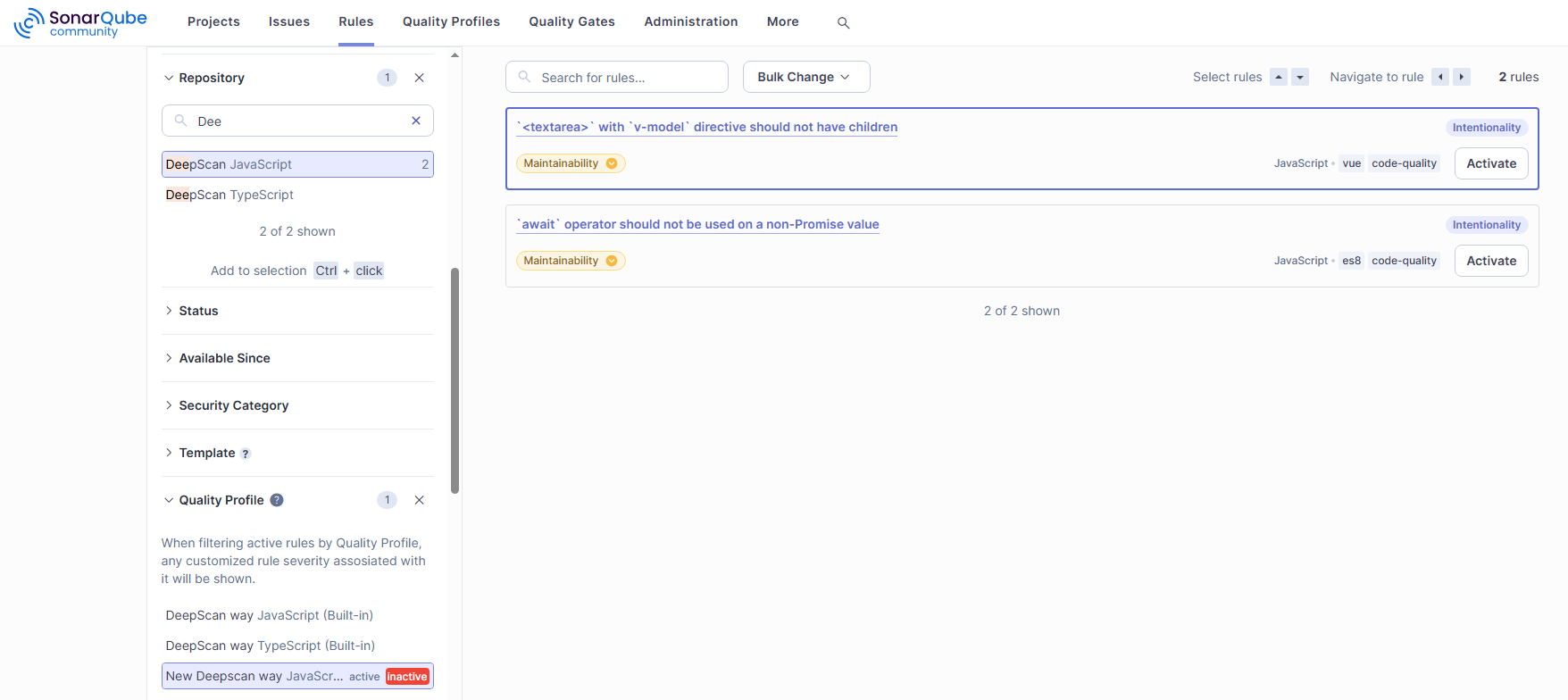
Now, you are in the Rules tab, where you can select rules to activate as follows:
- Select Repository > DeepScan in the left panel.
- In the list of rules on the right, click Activate button for the rule to activate.
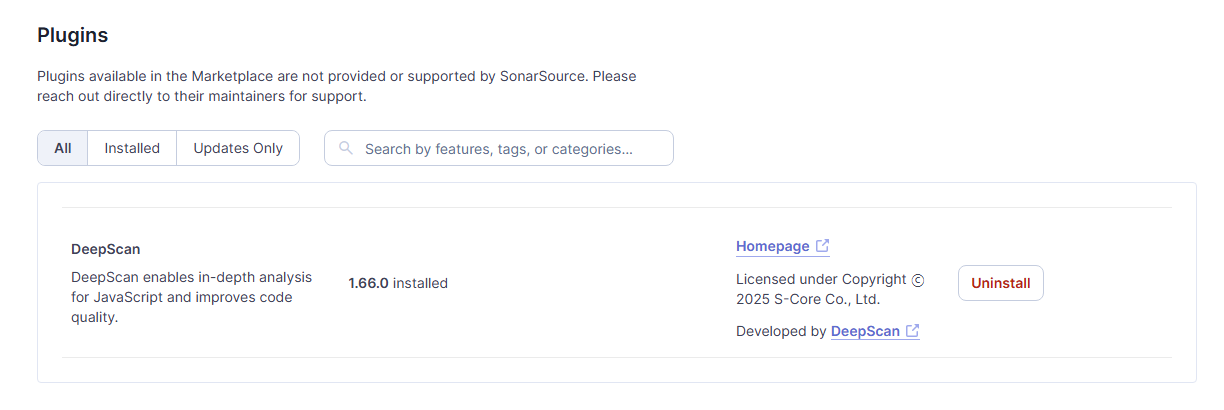
Uninstalling
You can delete an existing plugin in two ways.
- Delete the plugin file from the
pluginsdirectory and restart the SonarQube server. - In Administration > Marketplace, click Uninstall button that appears at the right of the installed DeepScan plugin.
Analysis
Analyzing a project
SonarQube consists of a SonarQube server (providing a database and dashboard) and a SonarQube Scanner (a tool analyzing codes and sending the results to the server).
So, to analyze your project, run the SonarQube Scanner.
Let's say you installed SonarQube Scanner in ~/sonar-scanner.
- Create a
sonar-project.propertiesfile in the project folder to analyze. (If you use other tools such as Maven, just follow the ways of those) - Run the following command in the project folder.
~/sonar-scanner/bin/sonar-scanner
- After the analysis is completed, the results are sent to the SonarQube server.
- Browse the results at the SonarQube.
An example of sonar-project.properties file is as follows:
- Source files are located in the
srcfolder. - SonarQube server is at
http://sonar.deepscan:9000and login account is "deepscan". - Display the project as "wordswarm-web" in the dashboard.
- Exclude
src/examplesandsrc/vendorsfolders from the analysis.
# Required metadata sonar.projectKey=wordswarm # Optional project properties sonar.projectName=wordswarm-web sonar.projectVersion=1.0 # SonarQube server url sonar.host.url=http://sonar.deepscan:9000 # SonarQube account if authentication is required sonar.login=deepscan sonar.password=deepscan # Comma-separated paths to directories with sources (optional) sonar.sources=src # Comma-separated paths to exclude sonar.exclusions=src/examples/*,src/vendors/* # Encoding of sources files sonar.sourceEncoding=UTF-8
Properties
Properties for the SonarQube analysis can be set in sonar-project.properties file or -Dkey=value arguments when running the SonarQube Scanner.
The general properties are as follows. You can refer a SonarQube documentation for more details.
| Property | Required | Description |
|---|---|---|
| sonar.projectKey | O | Unique project ID |
| sonar.projectName | Project name | |
| sonar.projectVersion | Project version | |
| sonar.host.url | Server URL | |
| sonar.token | Authentication token | |
| sonar.login | Login account | |
| sonar.password | Login password | |
| sonar.sources | Comma-separated folders to analyze. Defaults to the project folder if not specified. | |
| sonar.exclusions | Comma-separated files or folders to exclude. Relative to the project folder. You can refer a SonarQube documentation for more details. |
|
| sonar.sourceEncoding | Encoding of source files | |
| sonar.deepscan.enable | Whether to run DeepScan. When set to false and run, previously detected issues will be changed as fixed. |
Analysis Target
DeepScan analyzes the following JavaScript and TypeScript files:
- JavaScript:
*.js,*.jsx - TypeScript:
*.ts,*.tsx - Vue.js:
*.vue - ES6 Modules:
*.mjs
Exclusion
The following files are not analyzed by default in the plugin:
- All files under
node_modulesandbower_componentsdirectory. - Minified file:
*.min.js,*-min.js,*_min.jsor when average line length is greater than 200. - Automatically generated
*.jsfiles from TypeScript files. - Files over 30,000 lines.
- Files over 1.5 MB in size.
- Lines with length greater than 400.
CI Integration
SonarQube Scanner can be run in the various environments such as Jenkins, Maven, and Gradle.
You can refer a SonarQube documentation and configure it according to your workflow.
Rule Set
You can find all of DeepScan rules in:
- Quality Profiles > JavaScript > DeepScan way
- Quality Profiles > TypeScript > DeepScan way
Language
DeepScan internally applies the same rules for JavaScript/TypeScript files. However, SonarQube separates them into different languages. So, one DeepScan rule corresponds to SonarQube rules for JavaScript and TypeScript. For example, the INSUFFICIENT_NULL_CHECK rule corresponds to SonarQube rules as below:
- deepscan-js:INSUFFICIENT_NULL_CHECK
- deepscan-ts:INSUFFICIENT_NULL_CHECK
Category
The categories of DeepScan rules correspond to SonarQube as below:
| DeepScan | SonarQube | |
|---|---|---|
| Standard Experience Mode (Type) |
Multi-Quality Rule Mode (Software Quality) |
|
| Error | BUG | Reliability |
| Code Quality | CODE_SMELL | Maintainability |
Severity
The impacts of DeepScan rules correspond to the severities of SonarQube as below:
| DeepScan | SonarQube | |
|---|---|---|
| Standard Experience Mode | Multi-Quality Rule Mode | |
| High | CRITICAL | High |
| Medium | MAJOR | Medium |
| Low | MINOR | Low |
Note that the severity of an issue follows the severity of the corresponding rule.
For example of CONSTANT_CONDITION rule, DeepScan detects it as Medium or Low impacts depending on the context, but all issues have a MINOR severity defined in the SonarQube server. This is because the issue should have the severity which can be changed by a user.
Clean Code Attribute
Depending on the nature, DeepScan rules correspond to various Clean Code attributes. You can check the attributes in SonarQube Multi-Quality Rule mode.
Changing the Issue Severity
Developers and reviewers can configure the issue severity depending on their context or priority.
You can change it to any severity for each detected issue. Below is an example of changing the severity from Major to Minor.
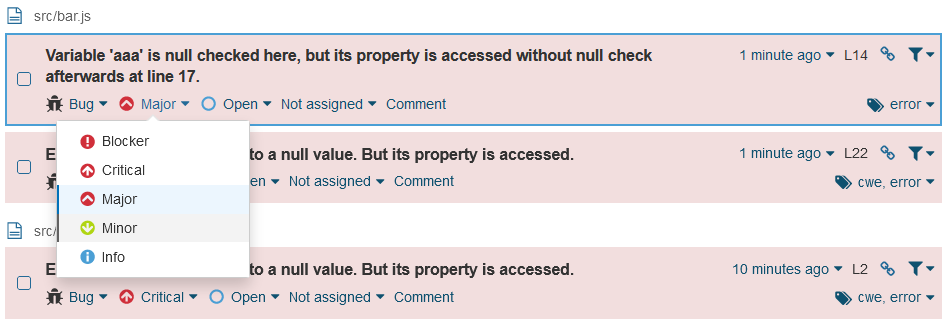
Changing the Rule Severity
When you want to change the rule severity itself, you need to create a profile derived from DeepScan way profile and change it.
A child profile inherits the rules of the parent profile and can set different severities. However, you can not deactivate a rule.
Below is an example of creating a child profile to change the rule severity.
- Create a new profile inheriting DeepScan way by clicking Quality Profiles > Create button.
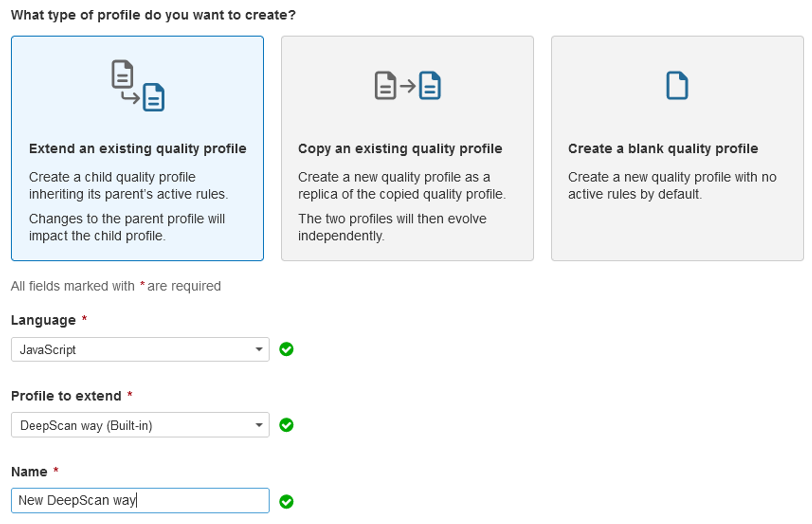
- All the rules of DeepScan way are inherited. Click on the rule to modify.
- In the rule details, you can change the rule severity by clicking Change button and set a new severity. Below is an example of changing Major severity to Minor:

- Set the project's JavaScript profile to a newly created one through the project menu Project Settings > Quality Profiles.
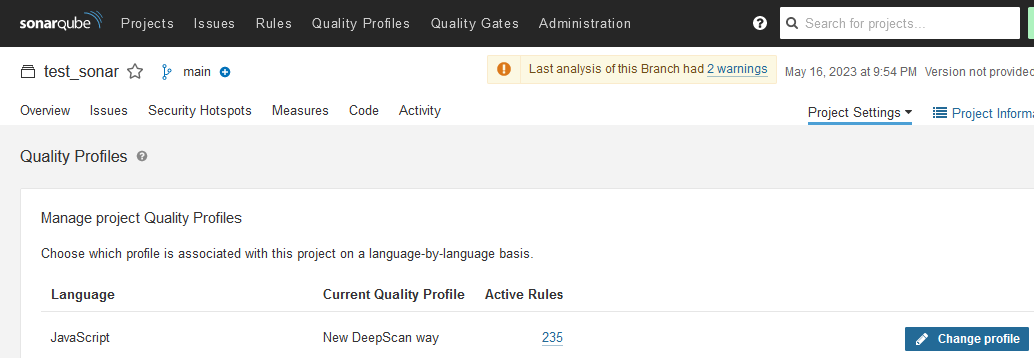
- Then analyze the project again.
Excluding rules
If you want to exclude some DeepScan rules, you can copy DeepScan way profile and deactivate unwanted rules, or create an empty profile and add only the rules you need.
Below is an example of creating an empty profile and adding rules having CRITICAL and MAJOR severities:
- Select Create a blank quality profile after clicking Quality Profiles > Create button.
- Select Activate More button of the newly created profile.
- Select Repository > DeepScan in the left panel.
- Select Default Severity > Critical in the left panel.
- Additionally select Default Severity > Major in the left panel with Ctrl + click.
- Click Bulk Change button at the top to add the selected rules to the new profile.
Dashboard
Measures
| Measure | Description |
|---|---|
| Analyzed Code Lines | Lines of code (number of lines excluding comment / blank) |
| Analyzed Total Lines | Total number of lines |
| Files | Number of files analyzed |
| High Impact | Number of issues with high impact |
| Medium Impact | Number of issues with medium impact |
| Low Impact | Number of issues with low impact |
| Issues | Number of all issues |
| Rating | DeepScan provides a grade which represent the quality status of your project. For more information, you can refer to Grade Rating. |